ONLINE ART GALLERY MANAGEMENT SYSTEM PROJECT REPORT
The main purpose of this project, entitled as “Online Art Gallery Management System” is to provide the facility of displays and sell art works of artist irrespective of their nationality, gender and other narrow consideration, through auction. Artist can register online for being a member in the art gallery and each artist can upload the digital copy of their art work under the respective categories. They can host their art work either for auction or for fixed price. The artist is liable to pay a fraction of the price of each art work to the web site to find the running fund for site.Art lovers have to go to the art exhibition to collect their favorite arts or painting.
Download Code
TABLE OF CONTENTS
S.no
|
Contents
|
Page no
|
1.
|
Project
Title
|
1-1
|
2.
|
Introduction
|
2-2
|
3.
|
Objective
|
3-3
|
4.
|
Survey of
Technology
|
4-5
|
5.
|
Project
Category
|
6-6
|
6.
|
Hardware
& Software Specification
|
7-7
|
7.
|
Design Specification
|
8-15
|
7.1
DFD Level 0
|
8-8
|
|
7.2
DFD Level 0 member
|
9-9
|
|
7.3 DFD Level 1 Artist
|
10-10
|
|
7.4
DFD Level 1 Admin
|
11-11
|
|
7.5
Context Diagrammed
|
12-12
|
|
7.6
Entity Relationship Diagram
|
13-13
|
|
7.7
Object Diagram
|
14-14
|
|
7.8
Activity Diagram for Member
|
14-14
|
|
7.9
Activity Diagram for Artist
|
15-15
|
|
8.
|
Database Structure
|
16-18
|
9.
|
Process Logic
|
19-19
|
10.
|
Modules
|
20-21
|
11.
|
Report Generation
|
22-22
|
12.
|
Future Scope
|
23-24
|
13.
|
Security Measures
|
25-25
|
14.
|
Bibliography
|
1.
PROJECT TITLE
|
|
Online Art Gallery
|
2. INTRODUCTION |
Online Art Gallery is
an online application, which is used to display and sell art works of artist
irrespective of their nationality, gender and other narrow consideration,
through auction. Artist can register online for being a member in the art
gallery and each artist can upload the digital copy of their art work under the
respective categories. They can host their art work either for auction or for
fixed price. The artist is liable to pay a fraction of the price of each art
work to the web site to find the running fund for site.Art lovers have to go to the art exhibition to collect their favorite
arts or painting. But now-a-days they are not getting enough time to go to the
galleries and collect the arts and paintings.
Existing System:
Customer can also register online
and they can browse art works that are arranged in different categories
scientifically. Each Customer can create their own gallery to see his favorite
art works with out much difficult. And each user has the right to purchase an
art work using the integrated payment gateway and participate in auction by
submitting their bids. Qualified bidder should remit the amount using payment
gateway and after each valid payment the art work will be shipped within some
days.
Proposed System:
ONLINE ART GALLERY
is a web application software and it is very helpful for the art lovers and
others who wants to know the addresses where this kind of arts will we sold.
This application
helps the end-users to search their arts and paintings and they can place order
for the selected pieces. The end-user can also get the information about the
art exhibition and the respective address, so, that they can visit to those
exhibitions.
3. OBJECTIVE
|
The objectives
of developing the Art Gellery are as given below: -
v
To store data of the
entire user who are registered in the site.
v
To solve the user’s
problem in time efficient manner.
Helping the user to search different Art with a robust search tools
v
To facilitate easy and
efficient retrieval of data as and when required for Art by the user.
v
Online updating of all type of Art, updating data using web based interfaces and with
the help of buttons and links in an easy and convenient way.
v
Data security is maintained to relatively high level by
implementing it at Database level, so as to ensure that only authorized users
have access to confidential User information.
v
Developing a viable candidate system that fulfill the Faster and
accurate information retrieval
v
Easy registration
v
Login dependent information retrieval and updating.Correct and
consistent maintenance of data and its quick retrieval
v
Improving the switches button and hyperlink so that the candidate
shall find all the queries they need at first sight.
4. SURVEY OF TECHNOLOGY
|
v SERVER SIDE COMPONENTS: ACTIVE SERVER PAGES
In
the world of web-accessible ASP.NET application Active server pages and
Servlets occupy a central position between enabled clients and application
servers. ASP working in the environment of the web container that provides
connection and services. By means of these connections, ASP control the
presentation of data derived from operations on database to network-connected
clients. This client role is suggested in figure-
HTML, Multimedia, XML Objects
Server presentation control
Binary files, Query, Result, XML
Business Logic
Back End Database
v SQL DATABASE MANAGEMENT SYSTEM
Database
systems have become ubiquitous across the computing landscape. This is partly
because of the basic facilities offered by database management systems:
physical data independence, ACID transaction properties, a high-level query
language, stored procedures, and triggers. These facilities permits
sophisticated applications to ‘push’ much of their complexity into the database
itself. The proliferation of database systems in the mobile and embedded market
segments is due, in addition to the features above, to the support for two-way
database replication and synchronization offered by most commercial database
management systems. Data synchronization technology makes it possible for
remote users to both access and update corporate data at a remote,
off-site location. With local (database) storage, this can be accomplished even
when disconnected from the corporate network.
SQL is a
realational database management system.
A relational database management
system (RDBMS) is a program that lets you create, update, and administer a relational
database. Most commercial RDBMS's use the Structured Query Language (SQL) to access
the database, although SQL was invented after the development of the relational
model and is not necessary for its use.
The leading RDBMS products
Microsoft's SQL Server.
Despite repeated challenges by competing technologies, as well as the claim by
some experts that no current RDBMS has fully implemented relational principles,
the majority of new corporate databases are still being created and managed
with an RDBMS.
5. PROJECT CATEGORY
|
“Web Based RDBMS”
The relational model was propounded by E.F. codd of the IBM in 1972. One
of the main advantages of the relational model is that it is conceptually
simple and more importantly based on mathematical theory of relation. It is
also frees the users from details of storage structure and access methods.
A
database can be understood as a collection of related files. How those files
are related depends on the model used. Early models included the hierarchical
model (where files are related in a parent/child manner, with each child file
having at most one parent file), and the network model (where files are related
as owners and members, similar to the network model except that each member
file can have more than one owner).
FUTURE OR RDBMS: -
ü
Data are the values stored in the database. On
its own, data means very little.
ü
A database is a collection of tables.
ü
Each table contains records, which are the
horizontal rows in the table. These are also called tuples.
ü
Each record contains fields, which are the
vertical columns of the table. These are also called attributes.
ü
Fields can be of many different types. There are
many standard types, and each DBMS (database management system, such as Oracle
or SQL) can also have their own specific types, but generally they fall into at
least three kinds - character, numeric and date
ü
The domain refers to the possible values each
field can contain (it's sometimes called a field specification).
ü
An index is a physical mechanism that improves
the performance of a database. Indexes are often confused with keys
ü
A view is a virtual table made up of a subset of
the actual tables.
6. HARDWARE & SOFTWARE SPECIFICATION
|
|
The hardware & software
specification and environment specifications used by programmers are:
HARDWARE:
ü Computer system: Standard pc/at
compatible with Pentium 3 or Pentium 4 CPU or more.
ü Primary memory: This Information
System works within 1 G.B. if user memory (RAM) addressed by MS windows.
ü Hard disk having 1GB free space.
ü Input device: Mouse & keyboard compatible with PC/ AT,
video adapters and monitors. It is a
colored program so better to use a colored monitor
ü Color monitors for best performance.
SOFTWARE:
ü Windows xp or above
ü Ms Visual Studio 2008
ü MsSqlSrver 2005
ü Internet explorer 5.0.
ü IIS 5.0 or above
ü The hardware & software
specification and environment specifications to run the application.
7. DESIGN SPECIFICATION
|
7.1DFD Level 0 :
7.2DFD Level 1 member:
7.3 DFD Level 1 Artist:
7.4 DFD Level 1 Admin:
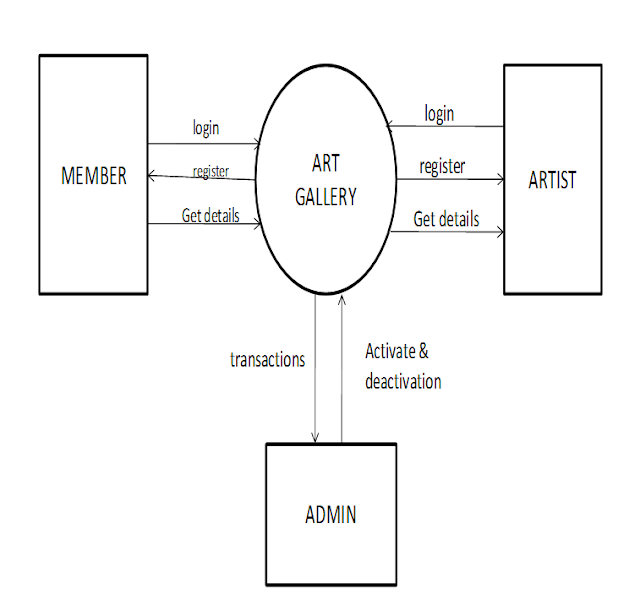
7.5 Context Diagram:
7.6ENTITY RELATIONSHIP DIAGRAM
7.7 OBJECT DIAGRAM
7.8 ACTIVITY DIAGRAM FOR MEMBER
7.9 ACTIVITY DIAGRAM FOR ARTIST
8. DATABASE STRUCTURE
|
v Login table
Field Name
|
Data Type
|
Size
|
Description
|
User id
|
Integer , Primarykey
|
10
|
User code
|
User name
|
Varchar
|
50
|
Name of the user
|
Password
|
Varchar
|
50
|
Password
|
User Type
|
Varchar
|
50
|
Type of the user
|
Security Code
|
Varchar
|
50
|
Security Code
|
Status
|
Varchar
|
50
|
Status
|
Date
|
Date/Time
|
Login date
|
v SoldArt
table
Field name
|
Data Type
|
Size
|
Description
|
SoldArtID
|
Int,Primarykey,Identity(1,1)
|
50
|
Auto Generated Sold Art Id
|
User ID
|
Int
|
50
|
User ID
|
Art ID
|
Int
|
50
|
Id of Art
|
Art Title
|
Varchar
|
250
|
Title of Art
|
Art List
|
Varchar
|
50
|
List of Art
|
Art Path
|
Varchar
|
50
|
Path of Art
|
Art Cost
|
Varchar
|
15
|
Cost of an Art
|
Date
|
Date/Time
|
Art Submit Date
|
v
Shipping
table
Field Name
|
Data Type
|
Size
|
Description
|
Shipping Id
|
Int,Primarykey,Identity(1,1)
|
Auto Generated Shipping Id
|
|
UserId
|
Integer, [Foreign Key]
|
10
|
User id
|
First Name
|
Varchar
|
50
|
First Name of User
|
Last Name
|
Varchar
|
50
|
Last Name of User
|
Gender
|
Varchar
|
50
|
Gender Detail of User
|
Email
|
Varchar
|
50
|
Email of User
|
City
|
Varchar
|
50
|
City
|
State
|
Varchar
|
50
|
State
|
Mobile
No
|
Varchar
|
10
|
Mobile no of User
|
Date
|
Date/Time
|
Date of Shipping
|
v
Contact
table
Field Name
|
Data Type
|
Size
|
Description
|
ContactId
|
Int,Primarykey,Identity(1,1)
|
Auto Generated ContactId
|
|
UserId
|
Integer, [Foreign Key]
|
10
|
User id
|
First Name
|
Varchar
|
50
|
First Name of User
|
Last Name
|
Varchar
|
50
|
Last Name of User
|
Gender
|
Varchar
|
50
|
Gender Detail of User
|
Email
|
Varchar
|
50
|
Email of User
|
City
|
Varchar
|
50
|
City
|
State
|
Varchar
|
50
|
State
|
Mobile
No
|
Varchar
|
10
|
Mobile no of User
|
Date
|
Date/Time
|
Date of Contacting
|
v
Card
Type table
Field Name
|
Data Type
|
Size
|
Description
|
Card
Checked ID
|
Int,Primarykey,Identity(1,1)
|
50
|
Auto
Generated Card Id
|
UserId
|
Integer, [Foreign Key]
|
User ID
|
|
Card
Name
|
Varchar
|
50
|
Name of
Card
|
Date
|
Date/Time
|
Date
|
v
Card
Type table
Field Name
|
Data Type
|
Size
|
Description
|
Art ID
|
Int,Primarykey,Identity(1,1)
|
50
|
Auto
Generated Art Id
|
UserId
|
Integer, [Foreign Key]
|
User ID
|
|
Art
Title
|
Varchar
|
150
|
Title
Of Art
|
Art Cost
|
Decimal
|
Price of Art
|
|
Art Path
|
Varchar
|
50
|
Path of Art
|
Date
|
Date/Time
|
Date
|
v
AddToCart
table
Field Name
|
Data Type
|
Size
|
Description
|
Cart ID
|
Int,Primarykey,Identity(1,1)
|
50
|
Auto
Generated Cart Id
|
UserId
|
Integer, [Foreign Key]
|
User ID
|
|
Art
Title
|
Varchar
|
150
|
Title
Of Art
|
Artist
|
Varchar
|
50
|
Name of
Artist
|
Art Cost
|
Decimal
|
Price of Art
|
|
Art Path
|
Varchar
|
50
|
Path of Art
|
Date
|
Date/Time
|
Date
|
9. PROCESS LOGIC
|
10. MODULES
|
The project include following main modules:
·
Login of the User and
·
Registration of user.
·
Art description.
·
User profile information.
·
The validation master
·
Report genaration
·
Brief description of the all modules.
Login of the Art Gellery -applicant and administrator
This module is considered with login of new user and
administrator. Every user must enter his some details about itself for login
the home page and after submitted he can Cart and ship Art online. The
administrator can also login from this module. He can insert, delete or update
the user login name and password.this module check the authenticity of the
person accessing the project. The main objective behind this module is to
provide security to the project so that access is restricted to the authorized
users.
Input is
taken as login and password that the user Enters.
This login
id and password sent back to the activeX exe through DLL to check the
information in the database.
If the
login id and password entered by the user matches those of the database file
then it will return and redirected to respective control panel, other wise give
a Error massage “login denied”.
v
Registration of
user: It takes the information the user and enter it into the
database. This module uses the table ‘Documantations for its operation
This table has following sub module.
- Add
- Edit
- Save
- Delete
v Art description: It takes the information form the Art and enters
it into database. This module user the table ‘Art’ for its operation.
This table has following sub module.
- Add
- Edit
- Update
- Delete
v Art info: It takes the
information form the user and enters it into database. This module user the
table. ‘ Art ’ for its operation
v
Artist profile info:It table the information the user enters it into database.
This module user the table ‘Arist for its operation.This table user has
following sub module:-
- add
- update
- delete
v
Validation master:This module validation the entry made by user if the entry
is not as per the specification a wrong message is given.
v Cart module:With the user of this
module user can cart the multiple arts simultaneously this modules user the
table ‘Passport and “Cart” for its operation.
11. REPORT GENERATION
|
v
Report generation: This system will
generate the report for the file software like. Following reports are
genreaded:-
- How many user are currently wring the site.
- How many Artist are are currently wring the
site.
- How many Art are are currently wring the site.
- Report on Purchased Arts.
- For Art seeker on the basis of Art search by
option.
- Search
by User Name.
- Search
by data
- Report of Shipped Records.
- Report on the basis of user perticulars.
- Report of the registered user who have user id
and password.
12. FUTURE SCOPE
|
Online User register facility could be brought on Web that
would enable the User to register and can see the detail in the system itself
by entering his login id No.
There should be some page like Payment Gateway, Cash on
delivery can give the better option forPurchasing an Art.
If user want to send Art detail to his friend then there is
option to mail Art detail to friend is necessary in Art page.
Each of these tasks serves describes the problem so that an
overall approach or solution may be synthesized.
1: Registered
Module:
In this module, User enters a login & password and the
software checks its validity. If the login & password is valid then he is
allowed to enter, otherwise “Invalid User/Password” message is displayed.
Different data access rights are assigned to different users.
2: Master Module.
This module is used to add and manage user, Art and Artist
Detaildetails etc.
3: Shipping
Module:
In this module, User purchased art and get this art his
location by shipping with two option, Online Cash Payment and Cash on delivery.
4:
Modifying/Updating Existing Entries:
In this module, whenever an existing entity is required to
be modified the corresponding forms are opened and the database is manipulated
and the data is fetched. Now the user can made the required changes and then
accordingly, he updates the data. Again, the checks are followed in case there
is any invalid entry.
5: Searching:
In this module, User can search on the requirement their
choice that mean, it (search engine) will help to search in all record/
information of available Art/Artist.
6: Validation of
Data Entered by the User & Error Handling:
In this module, the validity of data entered by the user
during the various business processes is checked through various validation
checks. For example, there should not be any characters entered in the numeric
fields, likewise if there is any error occurs than it should handle that
particular error and give the required messages.
|
13. SECURITY MESAURES
|
Security in database involves both
policies and mechanisms to protect the data and ensure that it is not accessed,
altered or deleted without proper authorization. Integrity implies that any
properly authorized access, alternation or deletion of the data in the database
does not change the validity of the data. The economic or strategic reasons for
protecting data from unauthorized access, corruption or destruction, there is a
privacy dimension for data security or integrity. Privacy is the ethical and
legal rights that individual have with regard to control over the dissemination
and use of their personal information.
Data has to be protected in the
database. There is a similar need for protection in a non database environment.
The operating system must ensure that files belonging to the database are not
used directly without proper authorization.
v
IDENTIFICATION AND AUTHORIZATION
The authorization mechanism
prepares the user profile for a user and indicates the portion of the database
accessible to that user and mode of the access allowed. The enforcement of the
security policies in the database system requires that the system knows the
identity of the user making the requests. This in turn requires that before
making any request, the user has to identify herself or himself to the system
and the authenticate identification to confirm that the user is in fact the
correct person.
v
AUTHENTICATION
The simplest and most common
authentication scheme used is a password to authenticate the user. The user
enters the user name or number and then authenticates her /him by the password.
A number of methods can be used in the authentication: by something known only
by the user, by something that only the user possesses, or by some
physical/physiological characteristics of the user.











No comments:
Post a Comment
Note: Only a member of this blog may post a comment.